Technology has overtaken our capacity for keeping up with it.
The industry is challenged from the continued reliance on legacy systems – an assumption of insulation from cyber threats..
If your organization is in need of cyber security professionals, we are here to assist.
Our security consultants can be available on demand, or full time to meet operational challenges.
Do we understand | Are we preparing | Can we sustain
With widely reported cyber-attacks on networks of mega shipping companies like Maersk & Anglo Eastern, cyber security awareness & the run to compliance is gaining momentum. The Maritime industry has been overtaken by technology, & while we are struggling to come to terms with it, cyber-attacks on maritime infrastructure are gaining critical momentum. In this article, I have tried to simplify the identification some of vulnerabilities existing onboard merchant ships, analyse them and look at the road ahead.
The writer is the CEO of eDOT solutions, which designs, implements & manages Cyber Security Solutions for ship owners & managers.
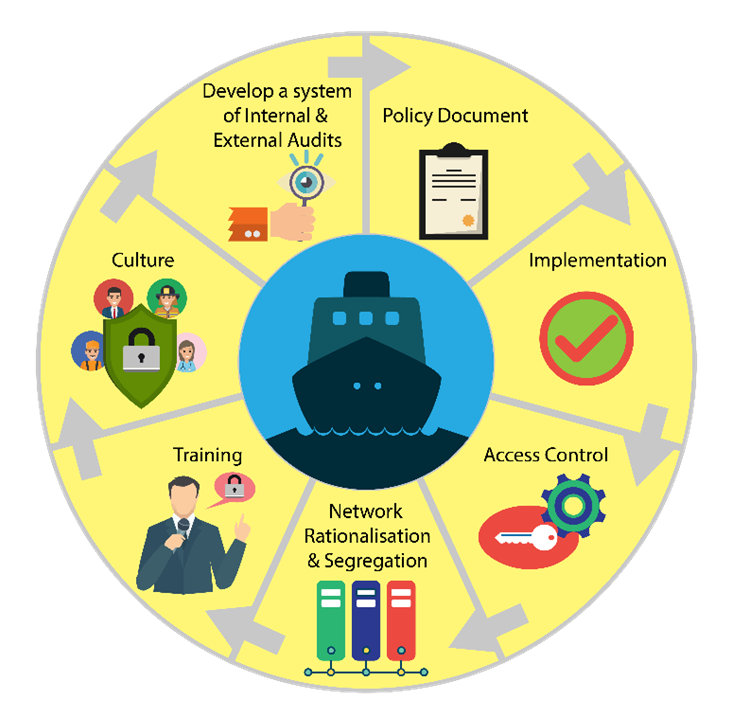
To organically identify associated cyber risks during ship operations; study, assess & analyse each risk considering it's impact on operations & business, and thus plan to either:-
Each with vis-à-vis cost and benefit ratio to be sustainable.
Cyber Security Project Managers
Cyber Incident Investigation Consultants
Network Access Control (NAC) Security Consultants
Penetration Testing Consultants
Firewall Consultants
Intrusion Prevention Consultants
Vulnerabilty Scanning Consultants
Risk Management
Vulnerability Management Consultants
Web Application Security Consultants
Compliance Experts
GDPR Consultants





Compliance with IMO RES 428, Class Certification VIQ7 & even 27001:2013 Certification would be achieved organically without any added effort or stress, It is relevant to note that understanding the concept of “operational technology – (OT)”, and its differences from ‘information technology (IT)”, is essential for estimating potential impact to operations and safety of the vessel.
These concepts are explained in my papers published earlier.
In recent times, the approach of the industry has been very subjective and diverse about OT near-miss reporting. This paper attempts to create a focused line of thought in identifying & reporting of Cyber Security related OT near-misses. In a small way, I hope it will help ship managers, as well as the sailing staff, in getting familiarized with the requirements of a Cyber Security Management System.
Recognizing, reporting and recording of IT near-miss & incidents is an integral part of the process, and is expected to go a long way in experiential learning of the seafarers, as well as educating the shore IT support staff about shipboard experiences and how to make the change in vocabulary & instruction-documents for better understanding of the seafarer.
